Public key vs private key cryptography is the twin-engine powering your online safety. These keys work together, but do very different jobs. Just like your email and its password, one is made for sharing, and the other is not. In this must-read guide, I’ll crack open the world of digital security, showing you how both keys play their parts. Get ready to understand how they lock up your info tight, and what makes them tick. If you ever use the internet, this is the knowledge you need. Let’s dive in and decode the secrets behind your digital locks.
Understanding Cryptography: Public vs Private Keys
The Fundamentals of Asymmetric Cryptography
Cryptography keeps our digital lives safe. It’s like a secret club with special handshakes. Only club members know them. In the world of online security, these ‘handshakes’ are called keys, and they guard our info from hackers. We use two main types: public and private keys.
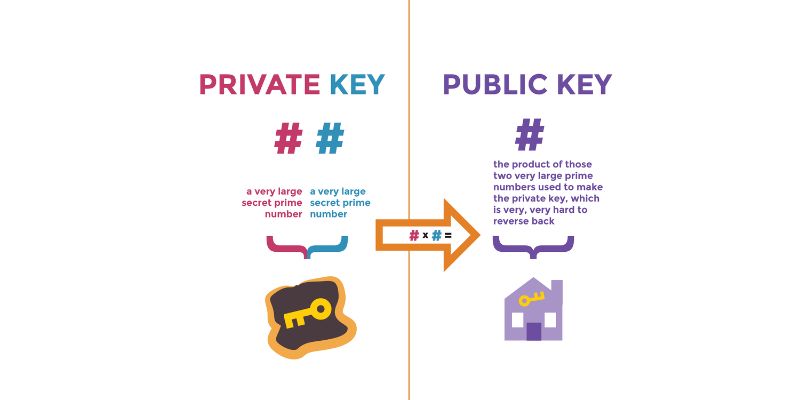
Public keys are like your home’s address. You give it out so people know where to send mail. Private keys are like the key to your home’s front door. It stays with you to keep your home safe.
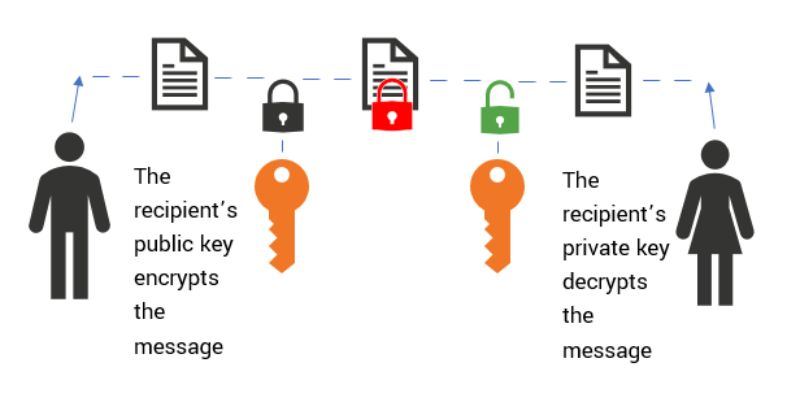
Public key encryption is when you use different keys to lock and unlock data. Think of a mailbox at the post office. Anyone can drop a letter in your box (encryption with the public key), but only you can take the letters out (decryption with your private key).
We call this asymmetric cryptography because the keys are different, not twins.
Distinct Roles of Encryption Keys in Data Security
Now, let’s chat about how these keys really matter in data security. To keep it simple, I’ll give you an example. Imagine you want to send a secret note to a friend. If you put it in a box with a special lock (public key), your friend needs the special key to open it (private key). That keeps the note just between you two.
Having two keys means more safety. What if someone else knows your public key? Well, it’s okay! They can’t unlock the secret note without the private key. It fits only one lock. That’s why you never share your private key.
For something like sharing web pages safely, there’s SSL/TLS encryption. When you visit a website with ‘https’ (the ‘s’ stands for ‘secure’), you’re using public keys to start a secret chat with the website. That’s how you know your info is safe while buying toys or checking emails.
Digital signatures use this cool key idea, too. They’re like a seal on a royal letter, proving it’s real.
We also have something called a certificate authority. These are the trusty folks who double-check the web’s public keys are true and right. That way, we can be sure we’re talking to the right person, not a trickster.
In our techy-world, encryption is a big deal. Public and private keys keep our digital handshakes secret and safe. They are heroes fighting the bad guys in the shadows of the internet. Thanks to keys, we can chill, knowing our pics, chats, and cat videos are safe from prying eyes.
Your friend’s address, the SSL/TLS, the secret notes—they all show why keys are big in our online world. They let us whisper across crowded rooms, safe in knowing only the right ears hear us. Just remember, keep your private key like your diary—just for you, locked away.
The Mechanics of Encryption: How Keys Work
Encrypting and Decrypting Data with Public and Private Keys
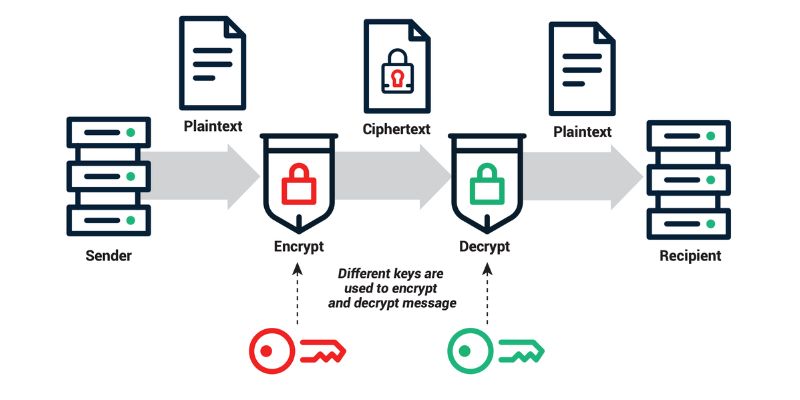
Imagine you want to send a secret note to a friend. You would need a special lock and key so only they can read it. That’s what public and private keys do in the digital world. Public key encryption explained simply is having two keys that lock and unlock data. One key locks, or encrypts, the data. This is the public key. The other key unlocks, or decrypts, the data. That one’s the private key.
Public keys are shared with everyone. They are like your home address; anyone can send you a letter. But, a private key is like the key to your front door. Only you have it, so only you can read the letters sent to you. This is where we see encryption keys differences. A public key encrypts data, and a private key decrypts it.
When we talk about private key encryption, we mean securing the key that does the unlocking. It’s a big deal because if someone gets your private key, they get your secrets too. That’s where the RSA algorithm steps in. RSA is a type of lock that is very hard to pick. It uses really huge numbers to keep your private key safe.
Sending a secret with this method means people can be sure it’s really from you. This is how we use digital signatures. They’re like signing your name on a letter but much safer.
And what about SSL/TLS encryption? This is the same idea but it’s like sending a locked box through the mail. The box is the secure website, SSL is the lock, and the keys are digital. When you shop online or check your bank account, you’re using this kind of lock and key to keep your info safe.
The Process of Key Pair Generation and Management
Let’s dive into how we make these keys. For encryption key pairs to work, they must fit together perfectly. Like making a puzzle piece that only matches one other piece. Key pair generation is like cutting out these puzzle pieces. Computers do this by mixing big prime numbers. Once you have your key pair, the next task is keeping them safe. This is key management.
Key management practices are like good habits for keeping your keys safe. Never share your private key, like you wouldn’t share your house key. And always know where your keys are. If you lose them, it’s big trouble.
Cryptography in cybersecurity is like having the best locks on your doors. With the right keys and locks, your digital secrets stay safe. That’s why we use things like PGP encryption for messages and HTTPS with public keys for safe websites. They’re top-notch locks that keep our data under wraps.
Remember, encryption is not just about locking away data. It’s about using the right keys to keep it safe and sound. Whether it’s your emails, your chats, or your personal files, encryption is the guardian of your digital life.
Cryptographic Algorithms and Protocols in Practice
From RSA to ECC: A Spectrum of Cryptographic Algorithms
Let’s dive into a world where secret codes lock away info. Think of these codes as special keys. Not your everyday house keys. They’re way cooler because they help keep your digital secrets safe. There’s a bunch of different keys. Each one comes from a big family of keys called cryptographic algorithms.
In this family, say hello to RSA and ECC. They help protect messages. RSA has been around for a while. It uses some math magic involving very large numbers to lock (encrypt) and unlock (decrypt) info. ECC is the new kid on the block. ECC can also encrypt and decrypt messages but it’s sneakier, working quietly in the background.
Both RSA and ECC make a perfect match for keeping your chats and files away from prying eyes. With RSA, you get solid protection. ECC steps up the game with the same protection but needs smaller keys to do the job. That means things run quicker and smoother.
SSL/TLS and HTTPS: Protocols Empowering Secure Communication
Now let’s say you want to send a secret message over the internet. You’d use something called protocols. Protocols are like rules that help computers talk safely.
One of the top dogs here is SSL/TLS. Think of it as a super-secret handshake between computers. SSL/TLS sets up a safe path for your info. It’s like a bodyguard that makes sure nobody messes with your data while it moves from your computer to another.
When you see HTTPS in front of a web address, it means SSL/TLS is at work. HTTPS is your friend, telling you that your info is secure when you’re online. Like when you shop or chat with friends, HTTPS keeps your credit card number and messages locked up tight as they travel across the internet.
Remember the handshake? SSL/TLS not only guards your info but also double-checks that you’re talking to the right computer. It wants to make sure it’s not a bad guy pretending to be your bank or buddy online.
Now, how do RSA and ECC fit into this? They’re part of the handshake. They help check the IDs of the computers talking to each other. RSA and ECC are really good at making encryption keys that are super hard for bad guys to guess.
So whether you’re sharing memes or sending sensitive work emails, RSA, ECC, and SSL/TLS have your back, making sure your secrets stay that way – secret. And that’s what makes the digital world a safer place to play and work.
Enhancing Digital Security with Cryptography
The Importance of Digital Signatures and Certificate Authorities
Now, let’s dive into digital signatures. These are like your secret online handshakes. They prove it’s really you who’s sending a message. When you sign an email digitally, you use a special code. This code, or private key, locks the message. Only the person with the right public key can unlock it.
You might wonder, “How do we trust these keys?” Well, imagine you get a key to a secret club. You’re excited but unsure if it’s a trick. To feel safe, you check with a friend you trust who vouches for the club. That’s what certificate authorities do. They are like trusted friends in the digital world. They say, “This key is good. You can trust it.”
Public Key Infrastructure (PKI): The Backbone of Trustworthy Encryption
Public key infrastructure, or PKI, is like a digital ID system. It keeps our online world safe. Think of a school. Each person gets an ID card. It proves who they are. PKI gives your computer an ID. Just like at school, each ID is different.
PKI ties your ID (which is your public key) to your secret key. That way, when you send an email or visit a website, it’s like showing your ID card. It says, “It’s really me!”
They use PKI for lots of stuff like shopping online, sending work emails, or logging into your bank. It protects your info so only the right people see it. It’s like giving your friend a locked diary. Only they have the key, so your secrets stay safe.
All this keeps our data and chats secure. And when things are secure, we can have fun and get our stuff done without worry. And hey, who doesn’t like that?
In this post, we dived into the world of cryptography, starting with the basics of public versus private keys. These keys power the secure exchange of data online, and understanding them means grasping the essence of online privacy. We covered how these keys encrypt and decrypt our information, keeping our digital communication tight. Key pair creation is like making a set of exclusive passes for a secure info club.
Then, we explored the inner workings of encryption, noting how diverse algorithms—from RSA to ECC—play their roles in data protection. Secure protocols like SSL/TLS and HTTPS are the everyday heroes ensuring that our online chats and transactions are safe from prying eyes.
Lastly, we saw how digital signatures and certificate authorities form the pillars of our digital defense structures, with Public Key Infrastructure standing strong as the trusted backbone of it all.
Keeping data safe is no small feat, but armed with this knowledge about cryptography, we’re better prepared to protect our information. Remember, in the digital world, strong encryption is your best friend. Stay safe and encrypted!
Q&A :
What is the difference between a public key and a private key in cryptography?
Public key and private key cryptography is based on the use of two distinct keys for encrypting and decrypting data. A public key is made available to everyone and is used to encrypt messages before they’re sent. In contrast, a private key remains confidential and is used by the recipient to decrypt the messages. The relationship between the keys ensures that only the holder of the private key can unlock the encrypted communication, enabling secure exchanges over an insecure network.
How does public key cryptography work?
Public key cryptography, also known as asymmetric cryptography, involves a pair of keys where one is used for encrypting the data and the other for decrypting it. When a message is sent, the sender uses the recipient’s public key to encrypt the message. Upon receiving the encrypted data, the recipient uses their private key to decrypt it. This method allows anyone to send encrypted messages to the recipient while only the recipient can read them, due to the unique private key they possess.
Why can’t the same key be used for encryption and decryption in public key systems?
In public key systems, the same key cannot be used for both encryption and decryption because it compromises the security model of asymmetric cryptography. If a single key was used, anyone with the key could both decrypt and encrypt messages, which would make it no different from a symmetric key system and expose the secure communication to potential interception and decryption by unauthorized parties. The utilisation of two keys ensures one can be publicly known without compromising the security of the private key.
Is it possible to derive the private key from the public key?
In practice, it should be computationally infeasible to derive the private key from the public key. This is due to the mathematical properties of the cryptographic algorithms used, such as RSA, where the complexity of factorizing large prime numbers ensures the security of the private key. Both keys are mathematically related, but with the current state of technology and mathematics, obtaining the private key from the public one should not be possible for secure algorithms.
Why is key distribution important in cryptography?
Key distribution is a critical aspect in cryptography as it refers to the process of sharing keys in an encrypted manner. Securely distributing the public key is important because if an attacker manages to replace the public key with one they control, they could potentially decrypt messages intended for the rightful recipient. In private key or symmetric cryptography, secure key distribution is even more vital because the same key is used for both encryption and decryption, meaning anyone with the key can intercept and decrypt the messages. Therefore, ensuring secure and trustworthy key distribution methods is essential for maintaining confidentiality and integrity in cryptographic systems.