Man-in-the-middle attack on blockchain: It’s the digital heist plot twist no one saw coming. With the rise of cryptocurrencies, savvy cyber thieves have leveled up. They sneak into communications between you and the blockchain network, aiming to swipe your crypto. Understanding this cyber sleight of hand is crucial to keeping your digital treasure chest locked tight. In this post, I’ll unwrap the mystery unfolding within your blockchain transactions, reveal the shifty tactics of these digital middlemen, and arm you with knowledge. Are you ready to dive in and guard your crypto with a savvy edge? Buckle up—it’s time to render these blockchain bandits bankrupt.
Understanding the Threat: Man-in-the-Middle Attacks on Blockchain
How MITM Attacks Work and Their Impact on Blockchain Integrity
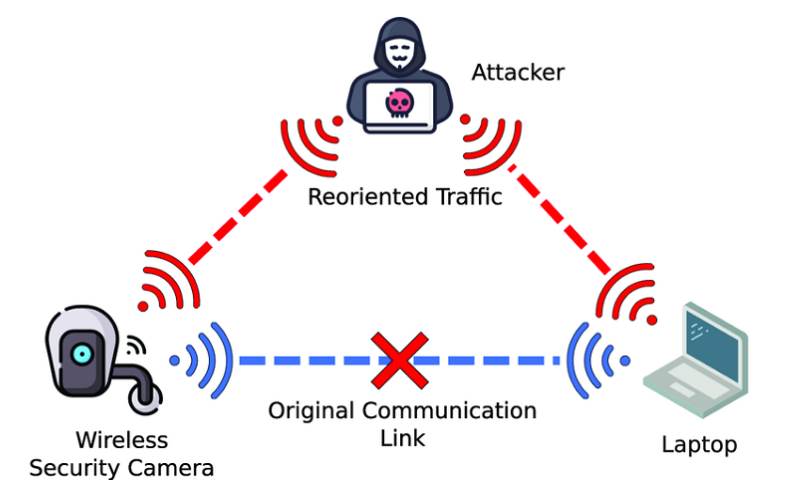
Man-in-the-middle attacks are sneaky. Bad guys slip between two parties in a transaction. They spy on or change the data being sent. It’s like someone secretly altering your mail before you open it. These attacks grab sensitive details or mess with data. This way, they can even steal your crypto.
Think of blockchain as a digital lockbox. Everyone watches to keep it safe. MITM attacks aim to break in. By intercepting data, they shake trust in blockchain’s security. For example, in a crypto exchange, they can fake a transaction. They trick you or the exchange. You send crypto to the wrong place. And it’s tough to undo these deals.
Blockchain encryption protects our crypto. It locks each block with a digital key. The goal? Keeping our assets safe from thieves. MITM attacks try to pick these locks. They can make us question blockchain’s reliability. But if we understand how these sneaks operate, we fight back better.
Recognizing Symptoms of Crypto Man-in-the-Middle Attack
Are you worried about MITM attacks? You should watch for signs. Maybe your crypto transaction is super slow. Or you spot strange warnings about security certificates. These could be clues.
Another hint is if you must reconnect to your crypto network. What’s happening? Someone may be cutting your connection. Then they pretend to be you or the exchange. It’s a key way MITM strikes. Your wallet might also show failed transaction alerts. These raise red flags too.
Spotting these signs gives us power. It means we can take action fast. Always check everything looks right with your transactions. This goes a long way in keeping your crypto secure. Remember, your money’s safety is as strong as the weakest link in the chain.
Our cyber defenses need to be top-notch. We must stay one step ahead of these crafty attackers. Encrypting our blockchain data is key. It’s like a secret code that only the right people can read. Wallet security is vital as well. It’s your personal guard against theft. By always using strong security, we keep our crypto safe and sound.
Knowing the foe means being ready to stand fast against attacks. MITM tricks are tough, but not unbeatable. With alertness and proper safeguards, we can keep our crypto safe and secure. Build your knowledge and your defenses to keep these attackers at bay.
The Cryptography Behind Blockchain Security
The Role of Encryption in Securing Blockchain Transactions
Picture a vault so tough, only you can open it. That’s what encryption does for your crypto transactions. Every time you send crypto, it gets locked up with a special code. This is like a secret handshake that only you and the receiver know. It keeps your crypto safe from prying eyes.
Secure blockchain transactions are a big deal. They stop hackers from grabbing your coins when you send them. Blockchain uses complex math to scramble your crypto data. This turns your sensitive information into a code that only the right person can read. Each piece of data is unique, like a fingerprint. So, no two transactions are the same.
This security isn’t just a fancy lock on a door. It’s a constantly changing puzzle that only the right key can solve. And guess what? You have that key when you make a transaction. But it’s not just any key—it’s a digital key that’s super hard to copy.
Digital Signature Security and Public Key Infrastructure Challenges
Now, let’s talk about digital signatures. These are like invisible ink that proves you sent the transaction. It’s a safety check that shows it’s really you. But it’s not as easy as just signing your name. Here’s where the magic happens—you have two keys.
You get a public key that everyone can see. It’s like your crypto address that people send coins to. Then, there’s a private key that only you know. This is your secret weapon. You use it to sign your transactions. It’s like giving them your okay. And because of the math behind it, no one can fake your signature. It’s that good.
But it’s not all perfect. Sometimes, bad guys find a way to mess with public keys. They try to trick the system and steal your crypto. That’s where we need to be smart and keep our keys safe. We’ve got to protect them like they’re gold because, in the crypto world, they are.
If you think about it, every time you use crypto, you’re trusting this system to work. You’re counting on those keys to keep your transactions safe from hackers. The whole thing is built on trust. The trust that no one can break the code or forge your digital signature.
Blockchain is amazing, and it can keep getting safer. With smart people working on it, we can keep the bad guys out. We just need to keep our keys secret and use the security that the blockchain gives us. It’s like building a stronger and stronger fortress around our crypto. And that’s pretty cool.
Proactive Defense: Mitigating Risks of MITM Attacks
Implementing Blockchain Safety Measures and Best Practices
We all want our crypto to be safe. So we must guard against man-in-the-middle attacks. These crafty hacks can mess with our crypto, but we can fight back. Here’s how we keep our blockchain secure. Working smart, using tight safety steps can stop these crafty intruders. First, we always encrypt our data. This means scrambling info so only the right person can read it. And we stick to best practices—just like brushing teeth to avoid cavities.
For you, this means knowing the ins and outs of wallet security. Keep your wallet’s key secret and safe. If you share it, it’s like opening the door to your digital cash. Watch out for warning signs. A slow network or strange warnings can mean trouble. Time for action! Keep your software up-to-date. Old software can be a weak spot, like a cracked wall. Take care of your crypto the way you care for your bike or your toys.
The key tip: Be smart about clicking on links or downloading files. Bad links can be traps, like fake free toy offers that are too good to be true. If unsure, take a step back.
Strengthening Network-Layer Defenses for Peer-to-Peer Safety
Crypto lives on a network, so here’s what you should know. To defend against cyber threats, we make sure every exchange on the network is like a secret handshake. Only those who know it can talk. This stops nosy strangers from poking in.
Our defenses stay tough. Think of it as a castle with high walls. We use tools that help us tell friends from sneaky strangers. HTTPS helps a lot—it’s like a strong gate that checks who comes into your castle. We do not want any unknown visitors in our crypto town!
We keep an eye on the public keys too. This is a bit like making sure only the right friend has the key to your secret club. If someone else gets it, it’s trouble. So let’s not let that happen.
Moreover, you have to understand how to spot an oddity in your transactions. Validating each transaction is like checking your homework before turning it in. It needs to be perfect to count.
In summary, crypto safety takes a team. From the developers making secure blockchain protocols, to people like you using them wisely. Stay alert, update often, and use strong security habits. You play a big role in keeping crypto safe.
Remember, every choice counts. From setting a strong password to avoiding weird links—it all builds a safer crypto world. Let’s keep our crypto street smart and secure!
Ensuring Transactional Trust: Verification and Protocol Integrity
Validating Blockchain Transactions to Thwart Unauthorized Changes
Validating blockchain transactions is key to keeping them safe. When you send crypto, you trust no one changes it secretly. That’s crucial for making sure you keep your money secure. But how can we know that no one is messing with our crypto?
Simple. Each blockchain transaction comes with a special code. It’s like a digital stamp that no one else can copy. If the code on your transaction changes, it’s a big red flag. This means someone might be trying to play tricks.
Now, let’s talk about how you can make sure your transactions are not tampered with. Keep an eye on your digital stamp. No two stamps should be the same. If they match, someone might be up to no good.
For the nerds out there, the digital stamp is also known as a hash. When your transaction’s hash matches an old one, it’s called a hash collision. This is very rare but could mean trouble if it happens.
Adopting Secure Communication Protocols and Handshake Mechanisms
Next, let’s dive into how we keep the bad guys out of our chat with the blockchain. It’s like a secret handshake between your computer and the blockchain. Just like in the movies. You don’t want any villains listening in.
To stop them, we use secure communication. Think of it as a secret code you use to talk with friends. If anyone else hears, they won’t understand.
When your wallet talks to the blockchain, they check each other’s identity. It’s like asking for a secret word before passing a note in class.
Using this method, your info is changed into a code. This is done using math problems that are really hard to solve. To anyone peeping, it’s all jumble. But for you and the blockchain, it’s clear as day.
What happens if someone tries to slip into your conversation? Your wallet and blockchain will know. They notice if the secret handshake is off. This keeps your crypto safe as it moves from A to B.
Remember to always look out for these safety steps when you send or get crypto. It’s how we keep the digital world secure. And that means your money stays in your pocket.
In this post, we tackled man-in-the-middle (MITM) attacks and how they threaten blockchain’s trust. We learned how the attacks work and their signs. Encryption and digital signatures play big roles in making blockchain safe. Yet, challenges are still there.
But don’t fret! You can fight these risks. Use safety measures and toughen your network defenses. Always check your blockchain transactions and use secure communication rules.
Think smart, stay safe, and trust in blockchain shines again. Keep your crypto secure by being one step ahead. Your security is in your hands!
Q&A :
What is a Man-in-the-Middle Attack in the Context of Blockchain?
A Man-in-the-Middle (MITM) attack on blockchain refers to an unauthorized interception by attackers who insert themselves between two parties who believe they are directly communicating with each other. This allows the attacker to manipulate or steal data. In blockchain, this could involve altering transaction details, redirecting funds, or obtaining sensitive information.
How Can One Prevent Man-in-the-Middle Attacks on Blockchain?
Preventing MITM attacks on blockchain typically involves using secure communication protocols like HTTPS, implementing multi-factor authentication, and employing robust encryption for data in transit. It’s also crucial to maintain software updates, be wary of unknown certificates, and use VPNs to secure public Wi-Fi connections.
Can a Man-in-the-Middle Attack Compromise Smart Contracts?
While the immutable nature of smart contracts on the blockchain provides a certain level of security, MITM attacks can potentially compromise them by altering the information relayed between the involved parties. This stresses the importance of secure communication channels and vigilant contract auditing practices.
Are Decentralized Networks Completely Immune to Man-in-the-Middle Attacks?
No network is completely immune to attacks, including decentralized blockchain networks. While blockchain offers improved security through decentralization and encryption, vulnerabilities can still be exploited, especially in the ‘endpoints’ where users interact with the network.
How Does a Man-in-the-Middle Attack Differ on a Blockchain Compared to Traditional Networks?
On traditional networks, MITM attacks intercept and potentially alter the data being exchanged. In blockchain, due to the nature of distributed ledgers, altering data becomes more complex and noticeable. However, endpoints like wallets and exchanges, where users interact with the blockchain, can still be vulnerable to MITM attacks.