DoS Attacks on Blockchain: Can Your Crypto Survive the Onslaught?
Imagine this: you wake up to find your crypto assets are stuck, immovable. The culprit? DoS attacks on blockchain – a real risk that threatens to freeze your digital fortune. Sure, blockchain is strong, but like any fortress, it has its weak spots. Hackers know this, and they won’t miss a chance to strike. Trust me, I’ve seen it all – the chaos, the panic. But I’ve also seen smart folks dodge this digital bullet. Want to be one of them? You’re going to need to buff up your blockchain’s armor. Get ready – I’m about to show you how.
Understanding Blockchain Vulnerabilities and Security Threats
Identifying Weak Points in Blockchain Architecture
Ever wonder why a blockchain can break down? It’s like a fortress. Yet, crack can let invaders in. Every blockchain has weak spots. These are often in how it’s built, or the rules it uses to work. DoS attack prevention blockchain is key to patch these cracks. It helps stop bad actors from halting the network.
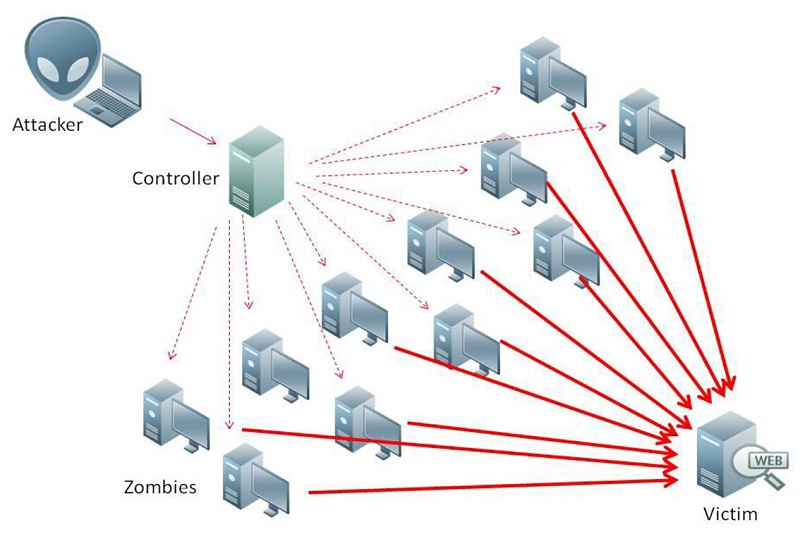
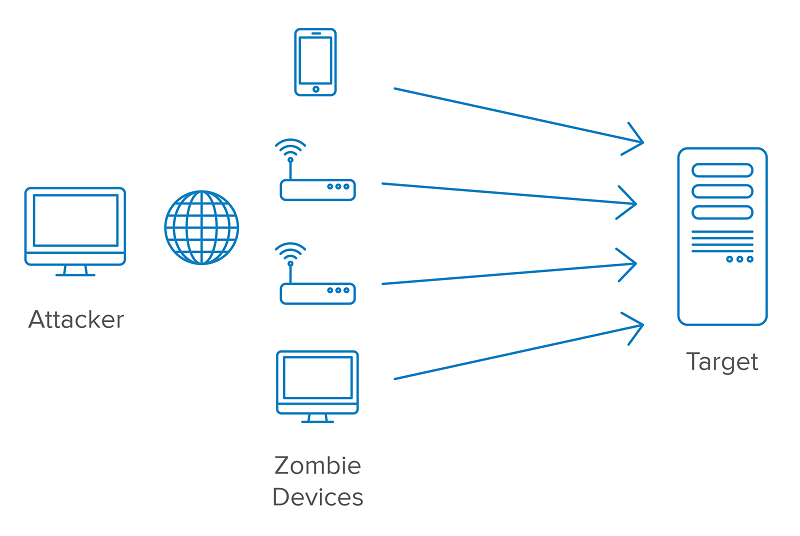
Blockchains face many risks, like DDoS, which aim to overload the system. Think of it like too many cars on a highway, causing a big jam. Attackers send lots of traffic to make the blockchain too busy to work right. Now, let’s dig deeper and find out more about these risks and how to keep your blockchain safe.
Common Attack Vectors: From DDoS to Smart Contract Exploits
Attackers go after blockchains in many ways. They often use DDoS to disturb the network. Our job is to guard against this, making sure the blockchain can still run smoothly. Other crooks may fool the code in smart contracts. This is why watching for weak code is a must. These bad contracts can leak money like a sieve.
We know attackers can cause trouble for blockchain. But what protects us? Crypto network disruption is less scary when defenses are up. One big defense is blockchain resiliency. This means making the network tough, hard to break.
Denial of service mitigation is another shield. It helps block the floods of fake requests. It’s like having a good doorman who only lets the right people in. We also know about decentralized ledger attacks. These are sneaky moves that disrupt our trust in the blockchain. Security threats in cryptocurrency can come from anywhere. The digital world is a wild place.
Attacks on distributed ledgers, like when someone tries to change the blockchain’s history, are bad news. We always look for signs of smart contract vulnerabilities. If we find one, we fix it fast. Hacking the hash rate in mining? That could let an attacker take over. We make sure miners can’t gang up and disrupt the chain.
Peer-to-peer network security keeps each connection safe. It’s like making sure every phone call is private. Scalability can bring DoS risks, yes. Blockchains must grow without becoming easy targets.
Consensus protocol security is key. It’s the heart of trust in blockchains. Without it, blockchains fall apart. Attackers might try a transaction flood attack, sending too much all at once. This could make the whole thing crash.
To keep things clear, I’m focused on stopping cyberattacks on digital currency. I ensure not even a single coin gets stolen. If someone tampers with the ledger, we all lose. That’s why we guard it well.
A Sybil attack in blockchain is one to watch out for. This is when fake identities swarm the network. Another biggie is the 51% attack risk. That’s when a group might control most of the network. Bad news!
But we’re on it. We work hard to keep node security in blockchain tight. We also build network layer protection. This keeps everything running.
Last but not least, crypto exchange DoS resilience is a big one. Crypto exchanges are where everyone trades coins. They’re a juicy target for attacks. We make sure they can keep trading, even when under fire. And that’s a quick look at the dangers blockchains face and how we fight back!
Strengthening Decentralized Ledger Defenses
Strategies for Enhancing Blockchain Resiliency
You love your crypto. So, we need to keep it safe from bad guys. I’m here to help. We’re talking about how to make blockchains strong against DoS attacks. DoS, or Denial of Service, is when someone floods the network. They send too much stuff and it can’t cope. So, everything grinds to a halt, just like traffic jams on the highway.
First off, let’s hit network security hard. It’s like putting a big guard in front of your door. He checks everyone, sees if they have an invite, and only then lets them in. We can do the same with our blockchain. We use lists of who’s okay and not okay. That way, we keep the troublemakers out.
Now, these blockchain vulnerabilities can be sneaky. Think about smart contracts. They are bits of code that live on the blockchain. They do stuff for us, like sending money when we tell them to. But, if they’re not written well, they can be a weak spot.
So, for those smart contract vulnerabilities, imagine we’re giving our code a helmet and pads. We check it and make sure it’s strong. That’s what a blockchain software audit is like. We go through it, find any weak spots, and fix them before they can be hit.
Implementing Effective Denial of Service Mitigation Techniques
Next up: the fight against DoS. There are cool ways to fight back. Think of DDoS blockchain protection like a superhero shield. It blocks the bad stuff so our network can keep running smooth.
One way to keep our ledger from getting jammed is rate limiting. That means we only let in a few people at a time. Like when you’re at a busy restaurant and there’s a wait to get a table. It keeps the place from overflowing.
Another thing we watch out for is this tricky thing called a Sybil attack. It’s when a bad guy pretends to be a bunch of users all at once. They try to take over the network that way. But we’re smart, we watch for it. We have checks in place so we know who’s real and who’s fake.
And the big one, the 51% attack risk, that’s when someone gets more than half the power in the network. They could change things and mess it all up. We keep our eyes peeled for anyone trying to grab too much control. We make sure power stays spread out so no one can boss the blockchain around.
To wrap it up, we make our blockchain strong like a castle. We build tall walls with network layer protection, keep the gates safe with node security, and have archers watching for ledger tampering. By using these strategies, we can keep the crypto kingdom safe, making sure every coin you’ve got can stand tall and brave when the DoS dragons come knocking!
Protecting Your Crypto Assets from Network Disruptions
Best Practices for Node Security in Blockchain
When we dive into blockchain, we often hear about its security. But even the toughest systems can fall victim to attacks—yes, even the mighty blockchain. Let’s chat about keeping your crypto safe from those sneaky network disruptions, shall we?
First things first, securing the nodes. Think of nodes like doors into a house. The more secure the doors, the safer the house. Nodes are access points to the blockchain network, so they need to be super strong against attacks. How do we do that? Well, there’s no magic spell, but there are some solid steps we can take.
The first step toward node security is to update software regularly. It’s like adding a fresh coat of paint to your door, but for security. Updates often patch up any known weak spots and keep the system tough against new threats. Next, limit access; not everyone needs a key to every door. The fewer people who have access, the less chance of someone leaving a door open for an attacker.
Then there’s monitoring traffic. You’ve got to keep an eye out for who’s coming and going. If you spot a crowd at the door all of a sudden, it might be an unwelcome party trying to crash your network. Encryption also adds a strong lock to your node doors. It scrambles up data so that even if someone gets a peek, they won’t understand what they’re seeing.
A robust firewall keeps the bad traffic out; think of it as a burly bouncer at your blockchain club. And let’s not forget about redundant systems. They’re like having a backup door in case the first one fails. They ensure that even if one system gets hit, the network keeps ticking.
Developing DDoS Blockchain Protection for Crypto Exchanges
Now onto our beloved crypto exchanges. They’re like the marketplaces of the digital currency world, and they need to stay open for business. But they’re hot targets for DoS attacks, which try to clog the system until it can’t handle any more traffic. It’s annoying, like when too many carts jam up at the store entrance, nobody can get in to shop!
To develop DDoS protection for these digital bazaars, we must get clever. First up, secure the infrastructure. Exchanges need strong defenses across all network layers. This includes specialized software that sniffs out and blocks bad traffic before it can cause a jam.
Creating a more spread out network helps too. This spreads the risk around, preventing one big target for attacks. Redundancy is also key here to keep the exchange up and running even when there’s trouble.
And then there’s the approach of letting only real customers in, like having a secret handshake. Verification methods can check if users are legit before they enter. Lastly, planning for scale is crucial. We need to make sure the exchange can handle loads of traffic, increasing capacity before it becomes a bottleneck.
These best practices keep your crypto hustle smooth and the blockchain robust. By locking down nodes and shielding exchanges, we’re building a fortress around our digital treasure. Let’s keep those safety measures tight and stay one step ahead of those looking to disrupt the crypto realm!
Advanced Security Measures Against DoS Attacks on Blockchain
Ensuring the Integrity of Consensus Protocols and Network Layers
You love your crypto, right? So we need to talk security—keeping your digital coins safe. A big threat is DoS attacks. These bad boys can stop a blockchain in its tracks. But don’t fret! There are smart ways to fight back.
First up, consensus protocols—think of them as the rules of the game for blockchain. They need to be rock solid. Why? Because if they’re weak, hackers can mess with the blockchain’s mind, so to speak. And we can’t have that!
To toughen up these protocols, experts like me work on the network. We play both defense and offense! Think of the blockchain as a fortress. To keep the bad guys out, every layer of its defense must be strong. If even one layer is down, your crypto could be at risk.
So how do we keep it all safe? Simple: we spot blockchain vulnerabilities before hackers do. It’s a bit like a game of hide and seek. We search every nook and cranny of the blockchain’s network security. And when we find a weakness, we fix it up better than before.
Deployment of Cryptographic Solutions and Rate Limiting Methods
Moving on, we have cryptographic solutions. They’re like secret codes that only you and your blockchain understand. These codes are super tough to crack. Hackers trying to DoS attack your blockchain with these in place? Good luck! It’s like trying to open a vault with a toothpick.
But wait, there’s more! We also use something called rate limiting methods. Imagine your blockchain is a club, and there’s a huge line outside. Now, let’s say you only allow a few people in at a time. This way, the party inside stays cool, and there’s no system overload.
Still, crypto network disruption is a mean beast, and it’s sneaky. Attackers use all kinds of tricks, like flooding the network with too many fake transactions. It’s called a transaction flood attack, and it’s a big no-no.
To stop this, we make the validation process smarter. It’s like having a bouncer that knows every regular’s face. If a stranger tries to crash the party, they’re not getting in!
Sometimes, attackers will try a Sybil attack in blockchain. They pretend to be many users at once. But we’re on to them. We make sure one user can’t pull too much weight. It keeps the system fair and keeps your crypto safe.
Now, you may have heard of the 51% attack risk. It’s scary, but our network layer protection has to be two steps ahead. We stay ready so that if such a massive attack comes, we can push it back.
And remember, we’re always on watch. No matter how the blockchain grows or changes, my job is to ensure it remains your trusty digital vault—resilient and secure. From mempool spamming to ledger tampering, no attack gets past us. Your crypto’s survival against DoS? It’s not just a hope; it’s the plan.
In this post, we dove deep into blockchain’s weak spots and ways people attack it. We looked at the bits that are not so strong in its design and the common tricks bad guys use, like messing up the system with too much traffic or breaking smart deals.
Then we moved on to beef up our blockchain shields. We explored tactics to make these digital ledgers tougher and ways to stop those big waves of traffic meant to shut us down.
We also zeroed in on keeping our digital money safe from those hiccups in the network. Solid steps for keeping our blockchain nodes secure and making sure our crypto trading places can stand their ground were key points.
To cap it off, we checked out top-notch security moves to guard against these nasty traffic jams in the blockchain world. We made sure we understand how super-important it is to have firm rules for reaching an agreement in our networks and putting locks and limits in place that only let the right kind of traffic through.
Remember, staying ahead of the threats means keeping our blockchain and crypto stuff secure. Keep these tips in mind, and you’re on the right track to shutting the door on the bad guys!
Q&A :
How Do DoS Attacks Affect Blockchain Technology?
DoS attacks, short for Denial of Service attacks, can seriously affect blockchain technology by overwhelming network resources, which can slow down or even halt legitimate transactions and activities on the blockchain. Although blockchains are typically more resistant to DoS attacks due to their decentralized nature, some vulnerabilities can still be exploited, particularly on smaller or less-secured blockchain networks.
What Makes Blockchain Resistant to DoS Attacks?
Blockchains are inherently more resistant to DoS attacks compared to traditional centralized systems because their distributed ledger is maintained across numerous nodes. This means that an attacker would need to incapacitate a significant portion of the nodes to affect the network fully. Furthermore, many blockchains utilize consensus mechanisms like Proof of Work (PoW) or Proof of Stake (PoS), which require computational work or stake to participate, deterring potential attackers by increasing the cost and effort needed to perform a successful attack.
Can Smart Contracts be Exploited to Perform DoS Attacks on a Blockchain?
Yes, smart contracts can sometimes be exploited to perform DoS attacks on blockchains. Vulnerabilities in a smart contract’s code can be identified and exploited by attackers to create conditions that either overload the blockchain or prevent specific transactions from being confirmed. This kind of attack often targets specific decentralized applications (dApps) rather than the entire blockchain network.
What Are Common Types of DoS Attacks in Blockchain Environments?
In blockchain environments, some common types of DoS attacks include transaction spamming, where the attacker floods the network with numerous low-value transactions to consume resources; block withholding, where a miner finds a valid block but does not broadcast it to the network; and eclipse attacks, aimed at isolating and attacking specific nodes within the network.
How to Prevent DoS Attacks on Blockchain Networks?
Preventing DoS attacks on blockchain networks requires a combination of proactive and reactive measures. Upgrading network protocols, constant monitoring for suspicious activities, employing anti-DDoS software, and adequately designing smart contracts to handle exceptional conditions are crucial steps. Additionally, implementing rate limits and fees for transactions can reduce the likelihood of spam transactions that might be part of a DoS attack. Ensuring decentralized applications and blockchain infrastructures are audited by security experts can also significantly mitigate the risk of such cyber threats.