Replay Attacks on Blockchain: Unpacking the Unseen Cyber Threat
Imagine finding out your blockchain transactions, the ones you thought were airtight, could be hijacked and reused without your consent. That’s the chilling reality of replay attacks on blockchain, an under-the-radar menace that could leave a dent in your digital wallet. As you dive into the blockchain ecosystem, it pays to know the nuts and bolts of these attacks. From the sneaky mechanics that make them tick to the various types buzzing around, grasping these details isn’t just geek talk—it’s your financial shield. So, before you make your next crypto move, let’s arm you with knowledge and strategies to spot and stop these unseen cyber threats dead in their tracks.
Understanding Replay Attacks in the Blockchain Ecosystem
The Mechanics of Replay Attacks
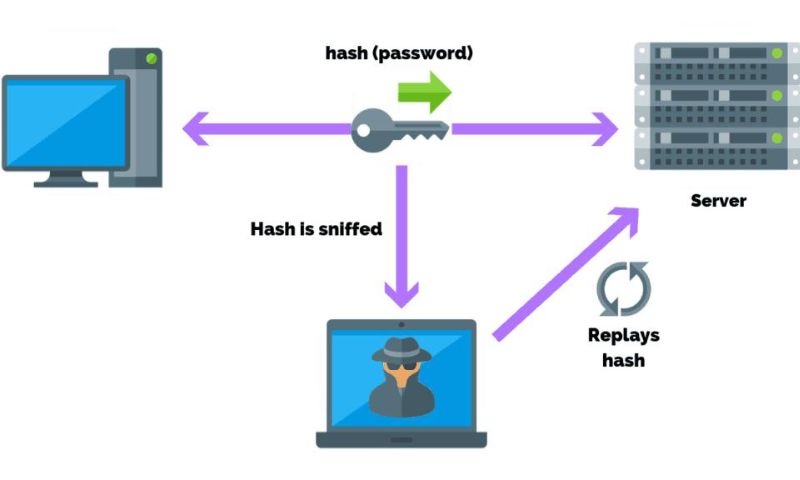
Replay attacks in cryptocurrency are like copycats. Imagine if someone copied your house key and kept entering your home. That scary thought is what happens with replay attacks, but with your digital money. They copy a transaction from one blockchain and do the same thing on another. A hacker might do this to spend the same money twice. That’s double spending in blockchain, and it’s bad news.
Think of a replay attack as an echo. The same thing happens twice without you wanting it to. Blockchain transaction verification tries to stop this. It checks if a transaction is fresh or just an echo. Blockchains have their security measures but they’re not perfect. Hackers are smart and blockchain security vulnerabilities can get missed.
Distinguishing Between Different Types of Replay Attacks
There are a few kinds of replay attacks. One you might have heard of is an Ethereum replay attack. This can happen after a hard fork. It’s when someone takes a transaction from the old path and replays it on the new one. This causes chaos and trust issues. A hard fork means a big change in the blockchain rules.
Another type is cross-chain replay attacks. These happen between two different blockchains. It’s like an echo bouncing from one wall to another. Here, we use unique identifiers, like nonces in blockchain, to tell each transaction apart. A nonce is a one-time number used for just one transaction. It helps everyone know that each transaction is special, like a signed note.
There are ways to stop these attacks. One way is by segregating transaction IDs. It means giving each transaction its unique fingerprint. These IDs help to spot the real from the copycats. Smart contract vulnerabilities add another twist. They are like deals you set and forget. Hackers can hunt for ways to trip them up. The deals need to be smart and secure. That’s where wallet security best practices come in.
I can’t emphasise enough on blockchain immutability. Once you put something on the blockchain, it should stay the same. It’s like writing in permanent marker. Replay attacks try to rub it out and write it again. They go against the whole point of the blockchain. Decentralized network risks like this can scare people away.
When we talk about securing blockchain, it’s all about layers. Keep every door locked. It’s your money and data on the line. Blockchain is strong but it takes effort to keep it that way. We always have to stay one step ahead of the bad actors, strengthening our defenses, and ensuring we keep our digital homes safe. Always remember, in the blockchain game, a robust security setup is your best defense against the copycats waiting in the shadows.
The Vulnerabilities and Risks Associated with Replay Attacks
Exploring Blockchain Security Vulnerabilities
Let’s dive deep into blockchain security weak spots. These are like unlocked doors for hackers. Imagine replay attacks in cryptocurrency as parrots. They copy, then repeat what just happened. So, if you pay in digital coins, they might make you pay twice without you knowing.
To stop this, folks use unique codes called nonces in blockchain. These codes are like one-time passwords. Each time you make a move, it’s like saying this move is fresh, not an old one. Smart right?
Now, hard fork implications are tricky. It’s like a group deciding to use new rules while others stick to old ones. If your digital cash hangs out in the middle, it could fall prey to copy-paste jobs across both sides.
Blockchain transaction verification can outsmart these copycats. They are like bouncers checking IDs at the door. They look at every bit of info, making sure only legit folks get through. This keeps your coin safe.
Ethereum replay attacks are sly buggers. They slip through the cracks when folks don’t see them coming. Like robbers in plain sight, they blend in until it’s too late. This is why double-checking every transaction is a must.
The Implications of Replay Attacks on Network Protocols
Network protocol security keeps the internet’s rules in order. Think of it as traffic lights on roads. If someone messes with them, chaos breaks out. Replay attacks do just that – they turn green lights into a mess of reds and yellows!
Let’s paint a picture. Alice sends Bob a digital note, signed and sealed. If there’s no guard watching, someone could send that note again, acting like Alice. This is what we call digital signature replay.
When it comes to cross-chain replay attacks, it’s like playing catch between two yards. You might think you’re safe because you’re playing in your own yard, but the ball can still end up next door. This happens when one blockchain talks to another, and they get their signals crossed.
Consensus mechanism flaws are like a group decision gone wrong. If they can’t agree, the bad actors have a field day. They take advantage of the confusion, sneaking in their mischief.
Now, cryptographic hash functions are like secret codes. No one can guess them, and they make sure each block in the chain is unique. This guards against the evil twins of the blockchain world – those pesky replay attacks that want to double-dip.
In the big picture, replay attacks show blockchain isn’t perfect. It’s a young tech, learning every day how to fight back. Like building muscle, it gets stronger every time we spot and fix a new weak spot.
To wrap it up, think of your digital wallet as your home. You wouldn’t leave your doors open, right? That’s what wallet security best practices are for – keeping your home and your coins safe and sound. Every step we take makes blockchain tougher, smarter, and ready for anything thrown its way.
Robust Defense Strategies Against Replay Attacks
Methods of Preventing Replay Attacks and Ensuring Transaction Integrity
Replay attacks in cryptocurrency can seem like ninja moves in movies. They are sneaky and harmful. Bad actors copy a transaction from one blockchain and reuse it on another. This spells trouble, especially after a blockchain splits, known as a hard fork.
We stop replay attacks by creating unique IDs for every transaction. This helps because it lets miners know each transaction is fresh and not a copycat.
For preventing replay attacks, we use a trick called a nonce. A nonce is a random number that’s used just once. It’s like a secret handshake for every deal you make. This stops bad actors from using old handshakes.
Utilizing Nonces and Advanced Cryptographic Techniques for Protection
Nonces in blockchain are top-secret numbers. They team up with unique codes called digital signatures. Together, they make sure every blockchain move you make is one-of-a-kind.
Digital signature replay is when bad guys copy your digital autograph. They want to use your blockchain moves for their gain. So, we use a cool thing called cryptographic hash functions. These turn your move into a secret code that only you know the full story to.
Smart contract vulnerabilities can be a headache. But by checking the code, we fix the weak spots. It’s like making super-strong armor for your digital deals.
Blockchain transaction verification is also key. It’s like a superhero team. They confirm every move is legit, before it’s set in stone.
In protecting against Ethereum replay attacks, it’s important after a hard fork. Both the old and new chains need their own rules of play. This way, ninjas can’t reuse moves on both playgrounds.
Wallet security best practices are simple things we do to guard our treasure. Like creating secret codes (passwords) and never sharing them. We also watch out for traps (phishing) from bad actors pretending to be friends.
Blockchain immutability means once something is written, it can’t be changed. Think of it as a magic book that locks in every story told, forever.
In conclusion, think of the blockchain like your own ninja dojo. You’re the wise sensei, always staying one step ahead of the sneaky ninjas, with your sharp moves and secret handshakes. By using these tips, you keep your dojo safe and your treasure secure.
Strengthening Blockchain Security Through Best Practices
Developing and Implementing Wallet Security Measures
Everyone knows that keeping money safe is key. In the digital world of blockchain, wallets need a shield too. This starts with what we call ‘wallet security best practices’. Imagine your digital wallet as a vault. You want only you to get in, right? That’s where strong passwords and safekeeping your private keys come in.
You also want to make sure nobody’s peeping when you’re checking your assets. That’s ‘network protocol security’. It keeps your connection to the blockchain safe. If bad folks can’t see what you’re doing, they can’t replay your transactions. Replay attacks are like copycats. They take what you did and try to do it again without you saying so. That’s a big no-no.
If your wallet says yes to transactions without checking twice, that’s asking for trouble. So ‘blockchain transaction verification’ is your wallet asking, “Are you sure?” every time you do something. This way, bad actors can’t use your digital signature again for their gain. It’s like a super picky bouncer at a club. Only the VIPs—your real transactions—get through.
Now, let’s talk about ‘hard fork implications’ and ‘Ethereum replay attacks’. When a blockchain splits into two (that’s a hard fork), things get muddled. One blockchain becomes two, and someone could play tricks with that. They can replay a transaction from one chain on the other. Those in the know work to stop this with ‘same-chain replay protection’.
‘Nonces in blockchain’ are another nifty trick. Think of a nonce like a ticket to a movie. It’s good for one show only. Once used, you can’t use it again. That’s how nonces help. They make sure each transaction is a one-time deal.
Creating a Layered Security Approach to Safeguard Against Common Blockchain Threats
Imagine your computer having more than one lock on it. Each lock checks a different thing. That’s ‘layered security’. We use it to keep the bad folks at bay. You have ‘cryptographic hash functions’ and stuff like ‘multi-sig transaction safety’ as locks. They make it harder for sneaky tricks like replay attacks to happen.
‘Smart contract vulnerabilities’ are a headache in blockchain security. Smart contracts are like promises in code. But sometimes, they’re not written well. Then, someone could take advantage of them. A layered approach checks each smart contract several times, in several ways.
And then there’s ‘consensus mechanism flaws’. This is about how all computers in the blockchain agree on what’s true. If this gets messed up, someone could fake a transaction. With layered security, several checks run to make sure everyone agrees the right way.
Lastly, there’s the ‘hash rate security factor’. I like to see it as guards watching over a treasure. More guards, more safety. The ‘hash rate’ is how many calculations the blockchain does to stay secure. The higher the hash rate, the tougher it is for attackers to mess things up.
In all, best practices are about being clever. They’re about putting up the right defenses at the right spots. This keeps your blockchain dealings safe as houses.
In this post, we dove into the complex world of replay attacks in blockchain. We unpacked how they work and the different types they come in. Remember, these attacks are serious. They can mess up network protocols and put blockchain security at risk.
You now know how to shield your transactions from replay attacks. Using nonces and smart crypto can help a lot. It’s like locking your door at night—you just do it to stay safe.
Always stay alert and use the best security for your wallet. Think of it as layers, each one makes you safer from common blockchain dangers. If you keep these tips in mind, you’re setting yourself up for a more secure blockchain experience. Stay safe and keep your transactions secure!
Q&A :
What are replay attacks in the context of blockchain technology?
A replay attack on the blockchain involves the malicious practice of taking a valid network transaction and repeating or delaying it to commit fraudulent activities like stealing tokens. Attackers can take advantage of such vulnerabilities during blockchain forks, particularly if no new measures are implemented to ensure transaction uniqueness across both chains.
How can blockchain networks prevent replay attacks?
To prevent replay attacks, blockchain networks can employ various strategies such as incorporating unique transaction IDs, using replay protection mechanisms, or implementing a technique called “splitting.” Splitting involves making a transaction valid on one chain and invalid on the other by distinguishing the ruleset of each chain. Additionally, network upgrades and strong consensus protocols provide layers of protection.
What are the risks associated with replay attacks on blockchains?
Replay attacks pose significant risks to blockchain assets and transactions, including double-spending, loss of funds, and reduced network integrity. These attacks can lead to financial losses for users and undermine the trust in a blockchain’s security. It is crucial for users to understand the potential risks and take necessary precautions during events like blockchain forks when the risk of replay attacks may be heightened.
Can replay attacks be identified and traced?
Identifying and tracing replay attacks can be challenging due to the nature of blockchain technology, which facilitates anonymity and decentralization. However, by monitoring transaction patterns and employing security measures that flag suspicious activities, such as identical transactions on different chains, it is possible to detect potential replay attacks. Advanced security tools are continually being developed to enhance monitoring and response strategies for such threats.
What steps should users take to protect their transactions from replay attacks?
Users can protect their transactions by ensuring they are using wallets and services that implement proper replay protection. It is advised to avoid making transactions immediately following a blockchain fork and to keep abreast of security updates and recommendations from their respective blockchain networks. Additionally, users can split their coins so that transactions are rendered invalid on one of the chains, further reducing the risk of replay attacks.